Ryerson Polytechnic University
Midterm Examination
CBIS504 Winter 1999
Suggested
Solution
Question 1
The computer processing portion
of a Sales Order system is represented by the a flowchart in the text Answer
the following questions:
a. What type of data processing
system is this? Explain and be specific. (5)
Response:
This is a batch processing system which uses direct access storage devices
rather than sequential tapes, but the records are stored in sequential files.
The transactions are keyed in, and the batch totals are calculated. The batch
totals accompany the sales order file through all the data processing runs that
follow. The edit run is used to test each record for the existence of clerical
or logical errors. Any records with errors are removed and written to an error
file to be corrected later by an authorized person. The batch totals are
recalculated for the "clean" transactions. The edited file is then
sorted based on the primary customer account number. The batch totals are used
to verify the integrity of the sorted database file. The sorted file is used to
update the accounts receivable file. The original accounts receivable file
remains in tact and is used for backup. The newly created accounts receivable
becomes the new master file. The customers' invoices are processed during the
update and billing run. The sales order file is sorted on the inventory number
so that the inventory master file can be updated. The original inventory file
remains in tact and is used for backup. The newly created inventory file
becomes the new master file. The batch totals are still used to verify the completeness
and accuracy of the transaction file. At the end of the day, the batch totals
are sorted and used to update the general ledger. The original general ledger
remains in tact and is used for backup. The newly created general ledger
becomes the new master file.
b. The auditor suggests that this
system can be greatly simplified by changing to direct access files, explain
the major operational changes that would occur in the system if this were done.(5)
Response:
If the sequentially stored data files are not used and real‑time
processing of data using indexed direct access files are used instead, the
editing and sort runs no longer become necessary. The transactions will be
immediately checked for input errors, and the accounts receivable file and inventory
files will automatically be updated as each transaction is processed. Thus,
batch totals will no longer be used. Accumulators may be used to accumulate
values which are periodically posted to the general ledger. The accounts
affected by each transaction in the master file will be overwritten with each
transaction that is processed.
c.
The auditor warns of control implications from this change that must be considered. Explain the nature of the control implications.(5)
Response:
Since the computers will be performing tasks that individuals used to perform,
such as inventory controls, the control procedures over program code need to be
secured from unauthorized access. The master files are overwritten each time a
record is processed. Controls should be put into place for periodically making
a backup copy of the master file, so that the records may be covered in case
the current working copy of a master file is destroyed or incorrectly
overwritten.
d. Sketch a flowchart (the
computerized portion only) of the proposed new system. Use correct symbols and label the diagram.
(10)
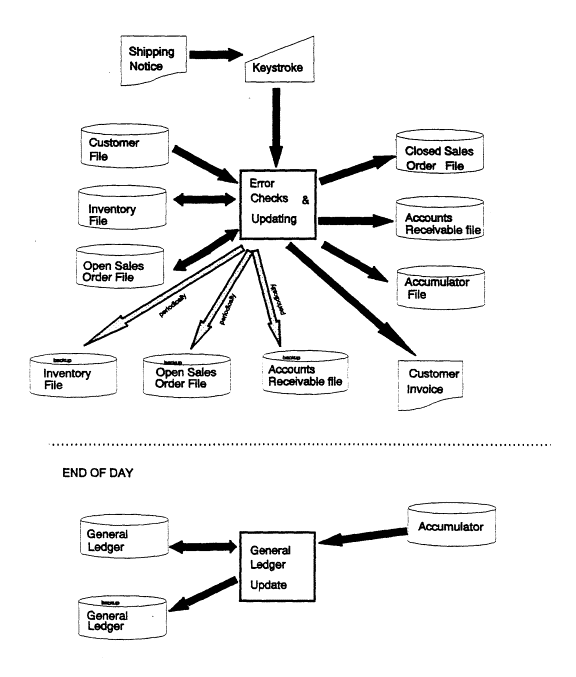
Response:
See diagram on the following page.
Question 2
2. Examine the diagram in the text and indicate
any incorrect initiation andlor
transfer of
documentation. What problems could this cause. (25)
Response:
The purchase requisition should originate from the inventory control department
after someone has reviewed the records to determine if and how much of an
inventory item needs to be ordered. If purchasing agents are allowed to
authorize purchase requisitions, they might be tempted to buy items not needed
in order to reap benefits and/or kickbacks from the vendor. The purchase order
which is sent to receiving is not indicated as a "blind copy", and
this might cause employees to either shirk their responsibilities and not count
the inventory or to steal some units since they know their value. Further,
receiving should retain a copy of the receiving report in their files along
with the purchase order and packing slip. The inventory control department
should not prepare a journal voucher to send to the general ledger department,
rather they should prepare summary information which the general ledger
department can use to reconcile the inventory control account with inventory
subsidiary summary. The accounts payable department needs to post the liability
to the accounts payable subsidiary ledger. The subsidiary accounts payable
ledger will not balance with the
control account in the general ledger if these postings are not made.
Question 3
3. Design a relational
data base system for a large costume rental store. The store
has approximately 3,200 customers each year. It is stocked
with over 500
costumes in various sizes. The rental costumes and other
items which may be
purchased by the customer (e.g., make‑up and teeth)
are purchased from
approximately 35 different suppliers. Design the necessary
data base files. Make
sure they are in third normal form, and indicate the
linkages necessary.
Response: Following is a list of database files unique to
this type of business. Additionally, traditional accounting files would be
necessary. The key fields used for linking are in boldface.
Costume Master Costume
Invento Customer
Master Vendor Master
Costume BD
Number Costurne
BD Number Customer BD Number Vendor BD Number
Description Copy Number Last
Name Company
Name
No. of Costumes Purchase
Date First Name Addressl
No. of times rented size Middle
Initial Address2
No. of times rented‑past year No. of times rented AddressI city
Vendor BD
Number Last
date rented Address2 State
Status‑checked
out city Zip
code
State
Zip
Code
Last
date rented a costume
Opgn Costume Transaction Lpg Closed
Costume Transaction. Locl Fine Loc
Customer BD
Number Customer ]D Number Customer BD Number
Costume BD
Number Costume BD Number Transaction Number
Copy Number Copy Number Amount Due
Date Rented Date
Rented Amount
Paid
Date Due Date
Due Date
Paid
Transaction
Number Transaction Number
Date Back
Sundries Invento Sundries
Transaction Lo‑q
Item Number Item Number
Description Quantity
Quantity on Hand Date
sold
EOQ
Safety Stock
Question 4
Response:
a. By integrating microcomputers with the company's
mainframe, the Milok Company should be able to realize the following
enhancements to information and report processing.
·
Processing
advantages. Routine, non‑routine, large and small analyses can be
completed by using the microcomputer with a typed copy as output. This
eliminates manual preparation and reduces the time required to prepare and
summarize reports. Furthermore, the typed output is more professional.
·
Data input. Data is
transferred from computer to computer at very high speed and accuracy rather than using a clerical data entry via a
keyboard. Downloading also eliminates any duplicate entry of data on two or
more systems.
·
Changes and
sensitivity analysis improved. Once a spreadsheet or database report is set
up/programmed, the effect of data changes or what‑if alterations can be
incorporated very quickly. The slow and inherently error‑prone function
of manual recalculation is eliminated because computer instructions are saved
and can be repeated.
·
Data reusability.
Because the data is downloaded onto a disk, it can be reused in its unaltered
form without going back to the mainframe. This can improve presentation and
decision activities.
·
Customization of
output. A microcomputer user can develop templates or small program routines
(also called macros) with a database or spreadsheet package to automate report
generation. This facility, which is normally done by a programmer on a
mainframe, can free the programmer for other work. This also speeds report
distribution and allows for the presentation of only relevant data.
b. By integrating microcomputers with a mainframe computer,
computer resource utilization will be altered in the following areas.
·
Special requests.
Nonroutine, one‑time reports can be done by a user rather than by a
special systems request. This resource reallocation is dependent on the amount
of data.
·
Programmer
utilization. Programmers will be freed from programming and maintaining users'
requests and allowed to focus on complete system or user department areas,
which form the base for users.
·
Hardware usage and
availability. For the people
involved with a micro/mainframe configuration, the role of the mainframe will
change from data storing, processing, and delivering to greater emphasis on
storing and delivering. A significant amount of processing can be done on the
microcomputer. This may or may not decrease the load on the mainframe as the
environment will begin to look more like real time rather than batch processing.
Such peripherals as terminals and high‑speed printers may be less needed
as microcomputer equipment is comparable in price and provides more
utilization.
·
Technical support.
The technical support function will need to be reviewed. Developments in both
the mainframe and microcomputer world must be monitored. System relations with
users must be cultivated as the systems department will take on a
consulting/instructing responsibility.
·
Systems and report
development. Through hands‑on experience, microcomputer users will
communicate better with the systems department. New systems can be designed by
the users on a small scale. This will give the user/requester a more intimate
knowledge of the system's requirements which should make for a clearer, tighter
specification.
c. The use of a micro‑to‑mainframe link will
greatly reduce the security of the original data stored on the mainframe as
follows.
·
Because of the nature
of microcomputers, there will be a general loss of centralized control such as
that previously associated with the operation of a mainframe.
·
Floppy disks can be
picked up and pocketed either accidentally or intentionally.
·
Because of their
nature, microcomputers are more accessible than terminals; therefore, a
microcomputer connected to another computer increases the risk of unauthorized
access to the other computer's data. Database administration and password
hierarchy and control must be more sophisticated and stricter to service the
wider uses of the system
·
Data could be
downloaded from the mainframe to the microcomputer, altered/ manipulated on the
microcomputer, and then passed back to the mainframe. Thus, the original data
on the mainframe could be changed. Without proper controls there might be no
audit trail and no way to detect what was done and by whom.