

| REPEATERS
As signals travel along a network cable, they degrade and become distorted in a process that is called attenuation. If a cable is long enough, the attenuation will finally make a signal unrecognizeable. A Repeater enables signals to travels farther. It works at the OSI's Physical layer to regenerate the signal of network and then resends the signal on other segments.
The repeater takes a weak signal from one segment, regenerates it, and passes it to the next segment. To pass data through the repeater in a usable fashion from one segment to the next, the packets and the Logical Link Control (LLC) protocols must be the same on the each segment. This means that a repeater will not enable communication, for example, between an 802.3 segment (Ethernet) and an 802.5 segment (Token Ring). Repeaters do not translate or filter anything. For a repeater to work, both segments that the repeater joins must have the same access method. The two most common access methods are CSMA/CD and token passing. A repeater cannot connect a segment using CSMA/CD to a segment using Token Passing. That is, they cannot translate an Ethernet packet into a Token Ring packet. BRIDGES Like a repater, a bridge can join segments or workgroup LANs. However, a bridge can also divide a network to isolate traffic or problems. For example, if the volume of traffic from one or two computers or a single department is flooding the network with data and slowing down entire operation, a bridge can isolate those computers or that department. |
Bridges can be used to:
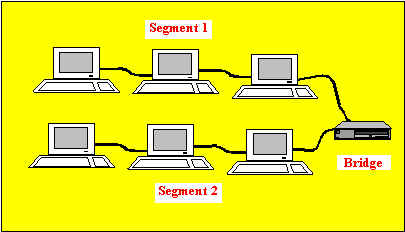
Bridges work at the Data Link Layer of the OSI model. Because they work at this layer, all information contained in the higher levels of the OSI model is unavailable to them. Therefore, they do not distinguish between one protocol and another.
Bridges simply pass all protocols along the network. Because all protocols pass across the bridges, it is up to the individual computers to determine which protocols they can recognize.
A bridge works on the principle that each network node has its own address. A bridge forwards the packets based on the address of the particular destination node.
As traffic passes through the bridge, information about the computer addresses is then stored in the bridge's RAM. The bridge will then use this RAM to build a routing table based on source addresses.
Creating a Routing Table
Bridges build their routing tables based on the addresses of computers that have trans-mitted data on the network. Specifically, bridges use source addressess?the address of device that initiates the transmission?to create a routing table.
When the bridge receives a packet, the source address is compared to the routing table. If the source address is not there, it is added to the table. The bridge then compares the destination address with the routing table database.
If a bridge knows the location of the destination node, it forwards the packet to it. If it does not know the destination, it forwards the packet to all segments.
- If the destination address is in the routing table and is on the same segment as the source address, the packet is discarded. This filtering helps to reduce network traffic and isolate segments of the network.
- If the destination address is in the routing table and not in the same segment as the source address, the bridge forwards the packet out of the appropriate port to reach the destination address.
- If the destination address is not in the routing table, the bridge forwards the packet to all of its ports, except the one on which it originated.
Segmenting Network Traffic
A bridge can segment traffic because of its routing table. A computer on segment1 (the source), sends data to another computer (the destination) also located in segment1. If the destination address is in the routing table, the bridge can detrmine that the destination computer is also on segment1. Because the source and destination computers are both on segment1, the packet does not get forwarded across the bridge to segment2.
Therefore, bridge can use routing table to reduce the traffice on the network by controlling which packets get forwarded to other segments. This controlling (or restricting) of the flow of network traffic is known as segmenting network traffic.
A large network is not limited to one bridge. Multiple
bridges can be used to combine several small networks into one large network.
ROUTERS
In an environment consisting of several network segments with different protocols and architecture, a bridge may not be adequate for ensuring fast communication among all of the segments. A complex network needs a device which not only knows the address of each segment, but also can determine the best path for sending data and filtering broadcast traffic to the local segment. Such a device is called a Router.
Routers work at the Network layer of the OSI model meaning that the Routers can switch and route packets across multiple networks. They do this by exchanging protocol-specific information between separate networks.
Routers have access to more information in packets than bridges, and use this information to improve packet deliveries. Routers are usually used in a complex network situation because they provide better traffic management than bridges and do not pass broadcast traffic.
Routers can share status and routing information with one another and use this information to bypass slow or malfunctioning connections.
Routers do not look at the destination node address; they only look at the network address. Routers will only pass the information if the network address is known. This ability to control the data passing through the router reduces the amount of traffic between networks and allows routers to use these links more efficiently than bridges.
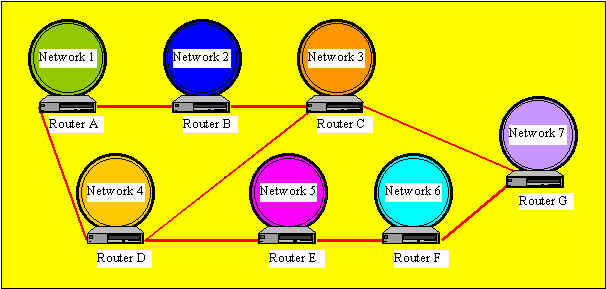
Routers require specific addresses. They only understand network numbers which allow them to talk to other resources and local network adapter card addresses. Routers do not talk to remote computers. When a router recieves oackets defined for a remote network, it will send them to the router that manages the destination network.
Using the router addressing scheme,
administrators can break one large network into many separate networks,
and because routers do not pass or even handle every packet, they act as
a safety barrier between network segments. This can greatly reduce the
amount of traffic on the network and the wait time experienced by users.
GATEWAYS
Gateways make communication possible between different architecture and environments. They repackage and conver data going from one environment to another so taht each environment can understand the other's environment data.
A gateway repackages information to match the requirements of the destination system. Gateways can change the format of a message so that it will conform to the application program at the receiving end of the transfer.
A gateway links two systems that do not use the same:
To process the data, the gateway:
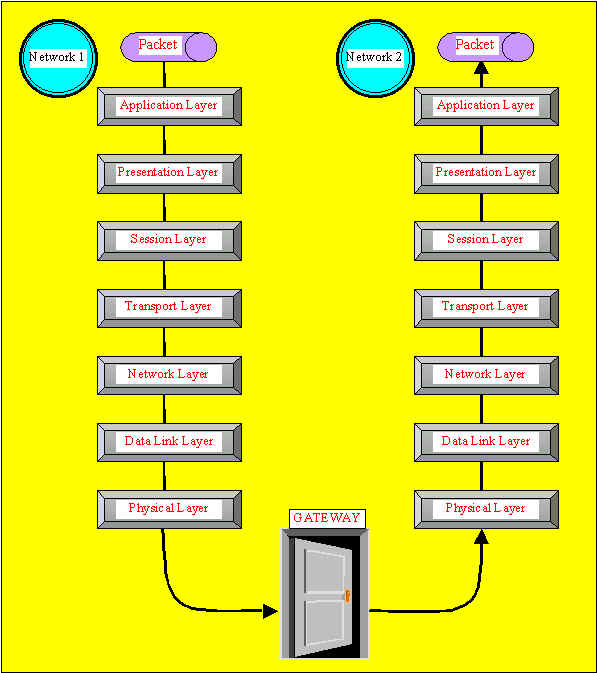
Some gateways use all seven layers of tyhe OSI model,
but gateways typically perform protocol conversion at the Application layer.
However, the level of functionally varies widely between types of gateways.